What significant improvements I can see after upgrading the gateway?
The upgraded version of the gateway maintains compatibility with SaaS upgrades. Few elements have in-depth monitoring templates.
What if the upgrade is not successful?
The platform is tested end-to-end for gateway upgrades. However, in case of failure, upgrades are rolled back.
What are the steps involved in upgrading the gateway?
- The gateway downloads the latest firmware from the cloud.
- the gateway installs the firmware. When the install is in progress, monitoring is stopped for two to three minutes. The tunnel is re-connected.
- The gateway is updated across all clients. The update requires less than five to 10 minutes per gateway.
Which disruptions are possible during the upgrade process?
During the upgrading process, when a gateway is updated, it is re-connected to the tunnel. For failures associated with connecting the gateway to the cloud, contact Support for assistance.
How long is each gateway down during an upgrade from start to finish?
The gateway upgrade consists of two phases: (1) Firmware download and (2) Firmware upgrade.
Phase 1: Firmware download
- Each gateway downloads its new firmware from the cloud.
- The gateway continues to run while the firmware is downloaded from the Cloud.
- The download time depends on the available network bandwidth – downloads are typically in the size range of 200-300 MB.
Phase 2: Firmware upgrade
- With this upgrade, the firmware is actually applied to the gateway.
- This process takes five minutes to complete.
- The gateway shuts down during this five-minute interval and does not monitor your devices.
- The gateway restarts itself after the firmware upgrade is complete.
While a gateway is being upgraded, which type of alerts are seen in the alert browser?
During the firmware upgrade, the cloud detects that the gateway is down and generates an alert with the subject Gateway is offline. This alert heals itself when the gateway is available again.
Which network ports are required for the gateway
Check the following list for network ports:
| Function | Port |
|---|---|
| SSH | TCP: 22 |
| Telnet | TCP: 23 |
| Agent to Gateway | TCP: 3128 |
| Gateway Web UI | TCP: 5480 |
| DHCP | TCP: 67 |
| SNMP | TCP: 161 |
| SNMP Traps | UDP: 162 |
| Rsyslog | TCP: 514 |
Can I install or update the software/packages on the gateway?
You should not install, update, or remove gateway software/packages. Doing so can lead to a gateway malfunction and OpsRamp is not responsible for fixing the problem. Also, you are not permitted to change any gateway configurations.
How to view the agent-installed resources connected via a gateway?
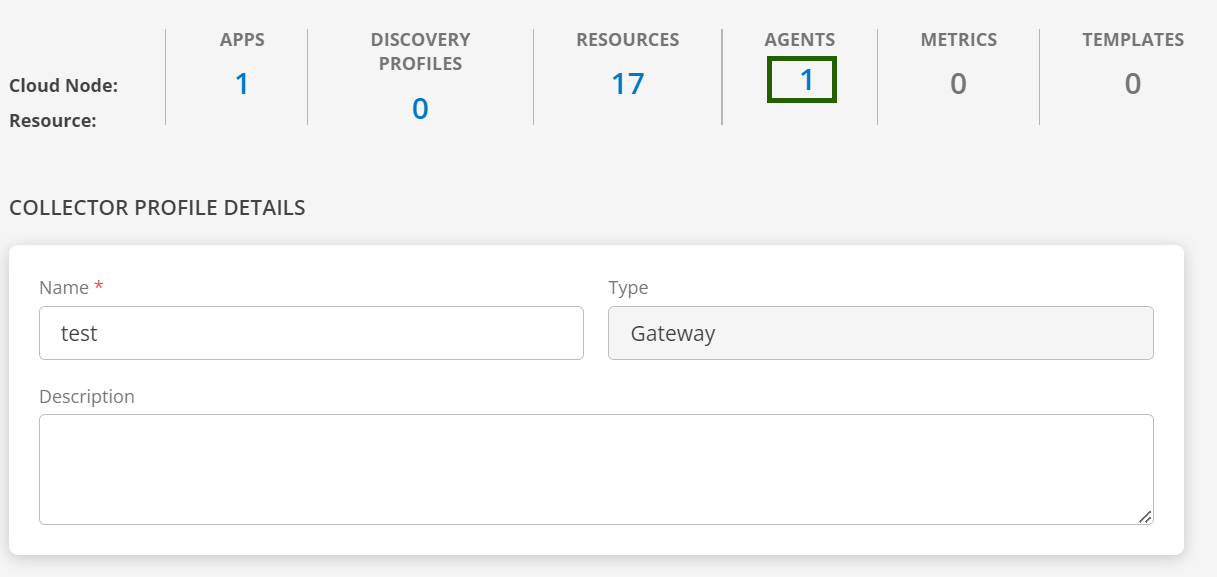
To view the agent installed resources connected via a gateway (proxy agent), follow the below steps:
- Navigate to Setup > Account > Collector Profile in the OpsRamp portal.
- Click on the Name of the collector profile. The collector profile details page will appears.
- Click on the Agent Count to view the list of agents connecting through the gateway.
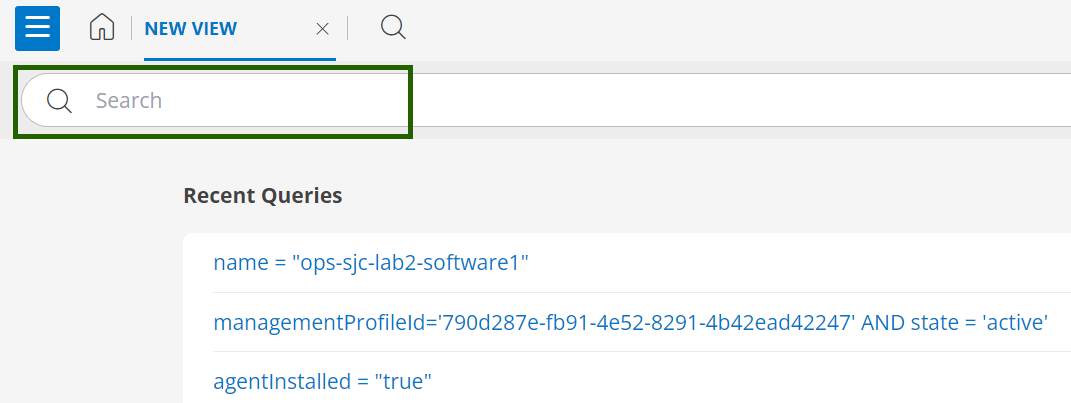
- Alternatively, navigate to Infrastructure > Search and click the search icon next to the home button in the top left corner. Here, you can use an OpsQL query to filter and view the same resources using the relevant agent attributes as listed here.
Attenuated Alert
Attenuated alerts are a mechanism designed to prevent a flood of alerts from a single source, such as a device or a specific metric, within a short timeframe. This helps to reduce alert noise and improve the signal-to-noise ratio.
key Benefits of Attenuated Alerts
- Reducing Alert Fatigue: Attenuated alerts help prevent an overwhelming number of alerts from a single source, making it easier for operations teams to focus on critical issues.
- Improving Alert Signal-to-Noise Ratio: By suppressing repetitive alerts, attenuated alerts help to highlight truly important events and reduce the number of false positives.
- Preventing Gateway Overload: Limiting the number of alerts sent to the cloud helps to prevent the gateway from being overloaded and ensures that critical alerts are always delivered.
How the Attenuated Alerts Work?
The following are the current behaviors of Attenuated Alerts, which apply only to the gateway:
- Throttling Limit: The gateway has a default limit of 4 alerts per 10 minutes that are sent to the OpsRamp Cloud. Any alerts beyond the 4th are held back and not sent until the 10-minute reset period ends. This applies to all alert severities, including Critical, Warning, or OK.
- Resumption: After the 10-minute reset period, the gateway resumes sending last saved alerts with the subject prefixed as “Attenuated Alert:” to indicate that the alert was previously suppressed.
Configuration
The alert throttling behavior can be configured in the vprobe.conf file:
Alert.throttling.reset.freq: Specifies the reset interval (default: 10 minutes).Alert.throttling.limit: Specifies the maximum number of alerts allowed within the reset interval (default: 4 alerts).
After adjusting these parameters, you need to restart the vprobe service to optimize the alert throttling behavior according to your specific monitoring requirements.
How to Fix the PowerShell 7.4.6 Issue in 19.0.0/19.0.1 Classic Gateway Patch?
Follow the steps below to resolve the PowerShell 7.4.6 issue in the patched gateway:
- Log in to the user account.
- Use the appropriate command to switch to root user (e.g., sudo -i or su depending on your environment).
- Run the following command to tag the necessary Docker image:
ctr i tag docker.io/library/opsramp-powershell:7.4.6 opsramp-powershell:7.4.6 - Run the script to verify the status of PowerShell:
/opt/gateway/powershell/powershell-check-status.sh - Ensure PowerShell is properly installed by checking the version:
pwsh --version - After running the above command, you should see the following output:
PowerShell 7.4.6
How to Subscribe to Ubuntu 22.04 LTS (Jammy) from the Amazon Marketplace?
- Log in to AWS Management Console
Open your web browser and log in to your AWS Management Console . - Navigate to the AWS Marketplace
From the AWS Console homepage, select Services > Marketplace or directly visit the AWS Marketplace . . - Search for Ubuntu 22.04 LTS (Jammy)
In the AWS Marketplace search bar, type Ubuntu 22.04 LTS or Ubuntu Jammy and press Enter. - Select the Ubuntu 22.04 LTS (Jammy) Listing
From the search results, click on the official Ubuntu 22.04 LTS (Jammy) AMI offered by Canonical. - Review Pricing and Terms
Review the subscription terms, pricing (usually free for the base AMI), and usage details on the listing page. - Click “Continue to Subscribe”
Click the Subscribe or Continue to Subscribe button. This will register your AWS account for the Ubuntu 22.04 AMI. - Accept the Terms
Accept the terms and conditions to complete the subscription process. - Launch the AMI
After subscribing, click Continue to Configuration to select your instance type, region, and other launch configurations. - Launch an EC2 Instance with Ubuntu 22.04 LTS
Follow the EC2 launch wizard to configure and launch your instance with Ubuntu 22.04 LTS (Jammy).
Syslog FAQs for OpsRamp Gateway
Q1. What types of logs does the OpsRamp Gateway collect and store in the syslog?
A: The gateway stores general system messages in the syslog.
Q2. Where is the syslog stored locally on the gateway?
A: Syslog messages are stored locally at the path /var/log/ on the gateway.
Q3. How long are syslog files maintained on the gateway?
A: The gateway maintains seven syslog files using log rotation. Each file has a maximum size of 10 MB.
Q4 Are syslog files sent periodically to the OpsRamp cloud?
A: No, syslog files from the gateway are not sent to the OpsRamp cloud periodically. However, customers can configure the gateway to forward syslog messages to their own central syslog server if desired.