Week of December 10, 2024 (18.2.0)
Common Gateway Updates
Enhancements
The following enhancements applicable to both Classic and NextGen Gateways:
- Added detailed discovery activity information for SNMP, Linux, and WMI discoveries. Users can now view how many devices are reachable and the number of successful SNMP, WMI, or SSH connections.
- Enhanced performance for monitoring VMware vSAN, providing improved efficiency and reliability.
- Added support for the following VMware metrics:
- vmware_cluster_host_down_count
- vmware_host_state
- Added XML-based configuration backup support for Palo Alto devices, enabling easier and more comprehensive configuration management.
Bug Fixes
Normalized the database connection pool size of Gateway monitoring applications with PostgreSQL to prevent database connection errors during high load conditions.
Classic Gateway
Enhancements
Added support for migrating vProbes between Java 11 to Java 17 and vice versa, from Java 17 to Java 11, providing greater flexibility in deployment and maintenance.
Bug Fixes
- In the current design we are sending Disk Size in the below format Ex: 40 GiB (42.94 GB) to OpsRamp portal where it will reflect the same in attributes tab. Now we changed the format to 42.94 GB from 40 GiB (42.94 GB) in the OpsRamp portal.
- Added a retry mechanism for Appliance Alerts sent from the Gateway to vProbe service. Previously, alerts (e.g., Gateway Registration, Service Check) failed if the vProbe service was down, as they were sent only once without confirmation. Now, the system retries up to three times to ensure successful alert delivery.
NextGen Gateway
Enhancements
Added support for users to specify the gateway pod placement by using a nodeSelector. This feature is available exclusively for Helm-based deployments.
Bug Fixes
Resolved an issue where NativeBridge logs were not generated or accessible properly in the NativeBridge container. This fix ensures that logs are captured accurately, improving visibility and aiding in troubleshooting.
Week of October 21, 2024 (18.1.0)
Common Gateway Updates
Enhancements
The following enhancements applicable to both Classic and NextGen Gateways:
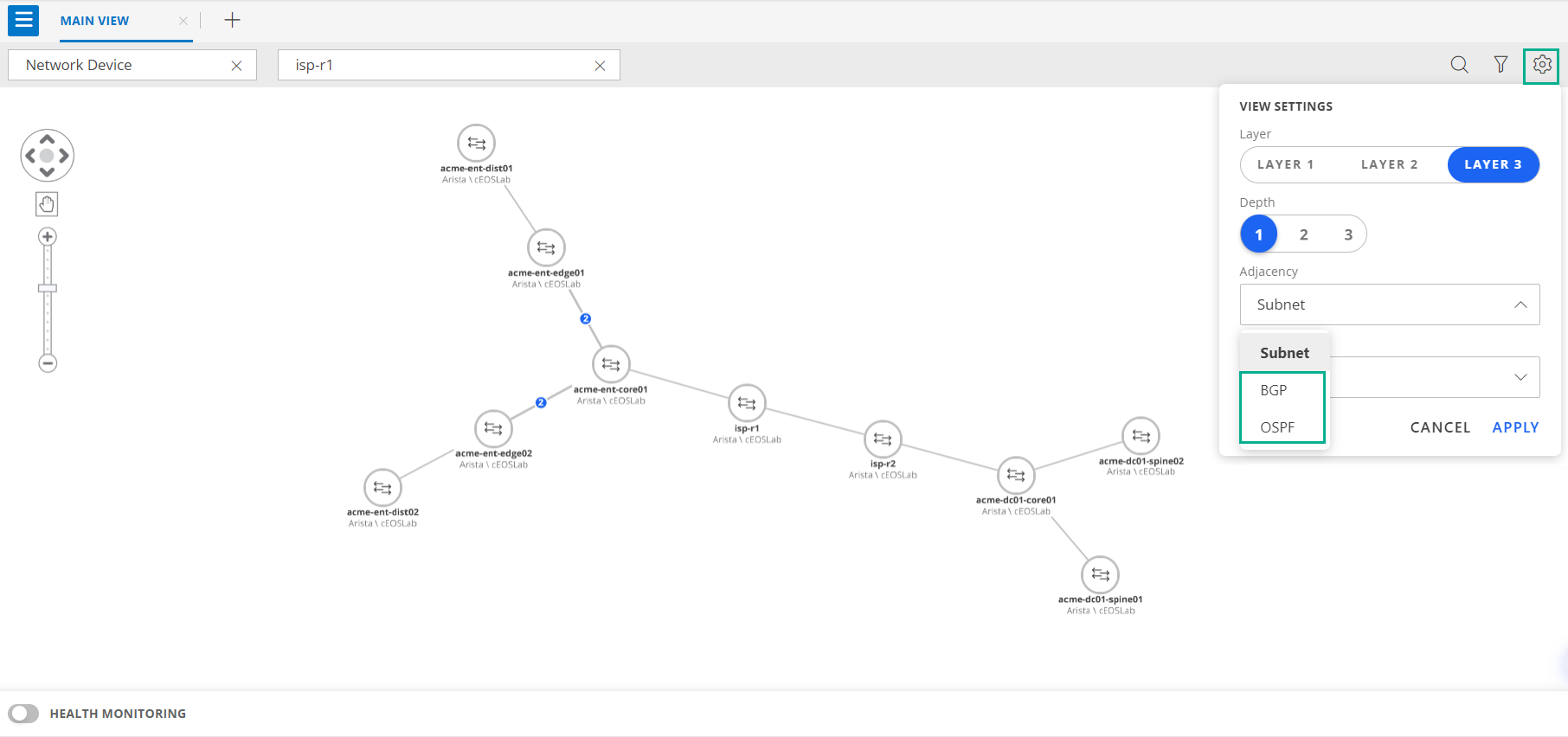
- Added support for visualizing BGP (Border Gateway Protocol) and OSPF (Open Shortest Path First) links within the network topology. This enhancement lets users easily view and distinguish between BGP and OSPF links, providing improved insights for Layer 3 network monitoring and analysis.
- Enhanced UCM (Unified Communications Manager) monitoring to work seamlessly with DNS (Domain Name System) names. This improves the flexibility and accuracy of UCM device tracking and management.
- Added support to automatically skip broadcast IPs during network discovery for specific subnets. This ensures a more efficient and accurate discovery process by eliminating unnecessary or unreachable addresses.
- Added support to collect and monitor disk partition metrics in vCenter Appliance environments, offering deeper visibility into storage performance and utilization.
- Implemented code changes to improve performance and reliability in gateway clustering, enhancing the scalability and stability of deployments using clustered gateways.
- Added support for monitoring XenServer virtual machines securely over HTTPS. This ensures a more secure connection while monitoring VM performance and status.
- Added support for displaying Connection State and Guest State attributes for virtual machines in VMware Classic APP. This provides better visibility into VM connection statuses and guest OS states for improved management.
Bug Fixes
The following bug fixes applicable to both Classic and NextGen Gateways:
- Fixed the issue where a new session was not created when the user updates the port in credentials.
- Fixed the issue that caused failures in trap monitoring when special characters were present in the configuration. Monitoring now fully supports special character inputs.
- Fixed the issue where snapshots were not consistently captured during XenServer monitoring, ensuring more reliable data collection.
- Fixed an issue that prevented XenServer monitoring from functioning correctly based on credentials configuration. Monitoring will now work as expected when proper credentials are provided.
Classic Gateway
Enhancements
Upgraded OS packages to the latest versions from the Ubuntu 2204 repository to enhance security.
NextGen Gateway
Bug Fixes
Resolved an issue where the NATS POD was missing for third-party app communication to vProbe in the Gateway patch from versions 17.0.0 to 18.0.0.
Known Issue
We are aware of a known issue in the v18.0.0/18.0.5 NextGen Gateway. Some customers experienced difficulties upgrading their NextGen Gateways from v18.0.0/18.0.5 to v18.1.0 through the OpsRamp UI. To resolve this issue, refer the document.
Week of September 12, 2024 (18.0.5)
Common Gateway Updates
Bug Fixes
Resolve an issue where alert states and metric data were not being saved from memory to the database. This issue affected alert functionality and metric data collection during vProbe service restarts.
Classic Gateway
Enhancements
Added support for retrieving AWS Cloud details with improved authentication mechanisms. This enhancement provides a more secure and efficient way to authenticate and access AWS resources
NextGen Gateway
Enhancements
We have added support for FQDN (Fully Qualified Domain Name) Load Balancers in the Gateway Squid Proxy. Previously, only IP address-based load balancers were supported, but now both FQDN and IP address load balancers are compatible.
Bug Fixes
Fixed an issue where proxy-based registration was not working for new Gateway deployments using version 18.0.0.
Week of August 14, 2024 (18.0.0)
OpsRamp Agent
Enhancement
- Introduced flag-based alerting for ‘Dell DRAC’ detection. This feature helps reduce unnecessary alerts for customers who do not need DRAC notifications.
- Enhanced CoreDNS Monitoring to include metrics collection from related ports across all Kubernetes distributions.
- Added support for StatsD monitoring in G2 Agent Template with a configurable StatsD port.
- Upgraded cryptography from AES-CBC to AES-GCM mode for better security.
- Added support for app roles in the MSSQL 2022 version.
- Improved data on installed software, including detailed OS and kernel information for Patch 2.0.
- Support for top 10 processes usage information using the process automation for the CPU metric alert (
system.cpu.usage.utilization).
Bug Fixes
- Resolved the 24-hour delay issue for alerts with empty subjects.
- Fixed agent shell deployment script installation issue with manually filled macros.
- Added support for Integration IDs in the deployAgent.sh script.
- Implemented vulnerability fixes in the following:
- Kubernetes agent YAML configuration
- Agent/Container-agent code during static code analysis
- jmxterm-1.1-OpsRamp.jar
- Kubernetes agent reported in OpsRamp Agent version 17.0 and above.
- Managed the default discovery of Docker containers by Linux VM Agents. You can now manually configure container discovery using the -d option if desired.
- Fixed issues with RSE Monitors to allow multiple RSE Monitors to operate concurrently on the server without hanging.
- Resolved the issue where handling of multiple colons in output, ensuring proper functionality of alert tokens in the OpsRamp Agent bash RSE for comma-separated values.
- Fixed issues with the PostgreSQL Monitor to properly read configuration parameters.
- Improved functionality for custom monitors, allowing multiple concurrent monitors on the server.
- We identified an issue with the Windows G1 Application monitors, which caused the topmost metric to display its state incorrectly. This issue has now been fixed.
Common Gateway Updates
Enhancements
The following enhancements applicable to both Classic and NextGen Gateways:
- Added support for monitoring IO Read, IO Write, and latency metrics on VMware hosts.
- Introduced configuration backup support for FPR-1150TD model devices.
- Enhanced RSE monitoring by including the complete exception in alerts, enabling easier identification of root causes through the alert description.
- Improved configuration backup functionality if the backup size exceeds 15MB.
- Enhanced SSH discovery to exclusively discover Linux distribution devices.
- The Synthetic Collector now supports sending the metrics to generate the latest Script Synthetic reports. This enhancement allows for detailed reporting of individual and grouped actions within an HTTP Synthetic transaction, addressing limitations in the previous version.
- In the Synthetic Application WebProbe, the
libcurlpackage has been upgraded from version 8.4.0 to the latest version 8.8.0. - New topology features were introduced in the Gateway 18.0.0 release. Customers who upgraded to Gateway 18.0.0 and those who want to utilize these new topology features need to perform a full SNMP discovery scan.
Bug Fixes
The following bug fixes apply to both Classic and NextGen Gateways:
- Fixed SNMP discovery issue with non-functioning component OIDs.
- Fixed parsing responses issue during VMware VSAN discovery.
- Fixed an issue with the NetApp Cluster Array RAID template.
- Fixed an issue to collect BGP Neighbors using the getNext method in SNMP discovery.
- Fixed “Template level components filtering” issue in RSE monitoring.
Security Fixes
Masked sensitive information in Squid Proxy to enhance security.
Classic Gateway
Bug Fixes
- Fixed disk size calculation issue for multi-partition deployments.
- Fixed the issue where the download logs option was not functioning correctly in the admin UI.
- Fixed an issue where the hostname for OpsRamp OVA could not be updated when deployed using the vApp option in VMware vCenter with a static IP address.
Security Fixes
- Updated the default password for the admin user. The new password can be found in the OpsRamp portal under Setup > Downloads > Gateway. This change applies only to newly installed classic gateways, not patched ones.
- Restricted file permissions for Squid and Nginx.
- Upgraded OS packages to the latest versions from the Ubuntu 2204 repository to enhance security.
- Downgraded the gateway’s run level (Run Level 5) to multi-user.target (non-graphical) to minimize the system’s attack surface by disabling unnecessary services.
Known Issues
If you are encountering issues with Static IP Configuration on the OpsRamp Gateway, refer the document.
NextGen Gateway
Note
Starting from version 18.0.0, when you deploy a new NextGen Gateway, it will be created as a separate device within the platform. However, this change only applies to new deployments. If you are updating an existing NextGen Gateway, it will continue to function as before without any changes.Enhancements
NextGen Gateway Support on Ubuntu 22.04 LTS OS
The OpsRamp NextGen Gateway 17.0.0 appliance was originally built on Ubuntu 20.04 LTS. With Ubuntu 20.04 LTS nearing the end of its life cycle and now deprecated, the NextGen Gateway appliance has been upgraded to Ubuntu 22.04 LTS Server. This upgrade ensures you benefit from the latest improvements and continuous security updates provided by Ubuntu 22.04 LTS.
Metallb Upgrade Support
The current OpsRamp NextGen Gateway includes an older version of the Metallb service. Starting with the 18.0.0 release, users can upgrade to the latest version of Metallb.
Note: If you are using an older version of Metallb, such as 1.0.0, you will need to upgrade manually.
See Upgrade Metallb to Latest Version document for more details.
Synthetics External Storage Class Support
Previously, the OpsRamp NextGen Gateway’s synthetics deployment only supported the default storage class. Starting with version 18.0.0, you can now specify an external storage class for synthetic deployments.
OpsRamp Agent Installation in HA Clusters
In earlier versions, the OpsRamp NextGen Gateway included the OpsRamp Agent on only one node. Starting with the 18.0.0 release, the OpsRamp Agent will be installed on all nodes in a high-availability (HA) cluster, as provided by OpsRamp (ISO/OVA).
Added support for Service Annotations
Added custom annotations in Helm Base Deployment for services like nextgen-gw-tcp, nextgen-gw-udp, and squid proxy.
Bug Fixes
Fixed an issue where cloud instances (AWS, GCE, Azure, OCI) and NextGen Gateway resources were not merging into a single resource.
Security Fixes
Removed Jetty Embedded Webserver and introduced light weight Netty HTTP Server to address security issues (CVE-2023-40167, CVE-2023-36478) caused by the Jetty Embedded Webserver.
Week of July 05, 2024 (17.2.5)
Classic Gateway
Enhancement
- Open ssh packages have now been upgraded to address critical vulnerabilities.
Week of June 13, 2024 (17.2.0)
Common Gateway
Enhancements
The following enhancements applicable to both Classic and NextGen Gateways:
- Enhanced Oracle DB monitoring to provide more specific authentication alerts. Instead of generic notifications. Now, alerts are sent for a particular instance by considering both the instance name and the monitor’s name. This helps you to:
- Identify the exact cause of authentication failures
- Reduce repetitive alerts
- Streamline troubleshooting efforts
- Added support for configuration backups to AOS-CX OS.
- Introduced events, volume utilization, and status monitoring support for Pure Storage.
- Added support to show SSD disk information for SSH-discovered devices.
- Added SSL support to PostgreSQL and MS SQL database monitoring.
Bug Fixes
The following bug fixes apply to both Classic and NextGen Gateways:
- Added fixes for Vnxe discovery and monitoring issues. Previously, responses from all Vnxe devices were stored in a single folder, causing problems. Now, a separate folder is created for each device to store response information.
- Resolved the issue where backup jobs were not deleted from the gateway database if the job has one device, and the device was removed.
Classic Gateway
Enhancement
Chrome packages have now been upgraded to address ZERO day vulnerabilities.
Week of May 18, 2024 (17.1.2)
Agent
Bug Fixes
- Resolved an issue where enabling IIS log management with agent log monitoring set to true resulted in CPU utilization reaching 100%. The system now operates efficiently without causing high CPU usage.
- Resolved an issue with the 64-bit Windows Agent installer that prevented handling of 32-bit registry paths for installed software. Both 32-bit and 64-bit software information are now correctly reported.
- Fixed an issue where the agent incorrectly identified devices as cloned due to case-sensitive system UUID comparisons. The agent now uses case-insensitive system UUID comparisons, ensuring existing alert entries are not mistakenly deleted after an agent restarts.
- Fixed an issue where agent logs displayed “unsupported charset in German locale ISO-8859-9” errors when deployed on Windows servers in Gebrüder Weiss. Support for the ISO-8859-9 charset has been added to resolve this issue.
- Resolved an issue preventing patches from being installed despite having the latest agent version on servers. This issue was caused by unnecessary comparison of patch names during installation, which was affected by dynamic changes in the system locale.
Week of April 23, 2024 (17.1.0)
Agent
Enhancements
- You can now choose to add a secondary proxy while downloading an agent for enhanced security. This is an optional feature. See Document for more information on secondary proxy and how to enable it.
- Added support for all German language locale types (de-at, de-de, de-li, de-lu, de-ch) to the agent. The agent can now read German characters.
- Enhanced the agent to support running scripts with both POSIX shell and bash scripting. Previously, the agent was limited to using only POSIX shell for running scripts by default.
Bug Fixes
- Fixed an issue where colons weren’t functioning in Alert tokens because the values contained multiple colons. You can now enter values with multiple colons in the alert tokens.
- The asset data showed a mismatch between the disk free space (available space) and the total disk space. This issue has now been resolved.
- Scripts with macros were failing because the cloud was sending the password in encrypted format. This issue has been resolved as the agent can now decrypt the password.
Common Gateway
Enhancements
The following enhancements applicable to both Classic and NextGen Gateways:.
- Introduced monitoring support for Pure Storage volume status. You can monitor the status of Pure Storage volumes and receive alerts regarding any status changes.
- Added multi-IP support for WLAN discovery. Discovery can now handle multiple IP addresses associated with WLAN devices.
- Introduced SSL certificate-based monitoring support to MSSQL and PostgreSQL databases to monitor the SSL certificates associated with the MSSQL and PostgreSQL database instances.
- Enhanced the alerting mechanism for VMware authentication failures. You can now receive more accurate and timely alerts whenever authentication failures occur in VMware environments.
Bug Fixes
The following bug fixes apply to both Classic and NextGen Gateways:
- Resolved an issue where adding a new performance metric to an existing VMware template was not functioning correctly.
- Fixed a typo error in Nutanix Host, Cluster Make, and Model Names, which was causing issues with Nutanix integration functionality.
- There was performance issue with VNXe Discovery and Monitoring across multiple integrations. The issue has been resolved and now it works smoothly.
- Fixed Netapp Cluster volume metrics issues, ensuring accurate reporting of volume metrics for Netapp Cluster storage systems.
Classic Gateway
Security Enhancements
Following are the security improvements in classic gateway:
- Fixed an issue where multiple X-Frame-Options headers were present in the gateway response. Now, the extra X-Frame-Options header has been removed from response.
- Fixed an issue where multiple X-Content-Type-Options headers were present in the gateway response. Now, the extra X-Content-Type-Options header has been removed from response.
- Fixed the Proxy Disclosure issue by disabling TRACE and TRACK on both the proxy and origin web server.
NextGen Gateway
Security Enhancement
Moved sensitive information from ConfigMap to Secrets ensuring higher level of security and protection of your gateway data.
Week of February 07, 2024 (17.0.0)
Agent Enhancements
Windows Agent Installation for Non-Admin Users
We are providing the Windows Agent installation with the following options to install the agent using user accounts:
- Default User: OpsRamp agent automatically creates a default user during installation.
- Custom User: You can provide existing user account credentials instead of using the default user during installation.
See Windows Agent Non-Admin Support for more details.
MicroK8s Support
From the Kubernetes Agent version 17.0.0, OpsRamp introduces support for MicroK8s discovery and monitoring. This enhancement allows users to leverage MicroK8s, a lightweight and scalable Kubernetes system, for deployment, scaling, and management of containerized applications.
See MicroK8s for more details.
Additional Metrics support for K8s-ApiServer Monitoring
The container agent has now extended its support to include the following metrics in K8s API server monitoring:
- Kube Apiserver Request Terminations Total
- Kube Apiserver Request Duration Seconds Count
- Kube Apiserver Request Duration Seconds Sum
- Kube Apiserver Up
See Kubernetes API server for more details.
Support for Custom Namespaces in Kube Metrics Server
Provided support for a custom namespace in the Kube Metric Server template. This improvement enables users to specify the desired namespace when applying the templates.
See Kubernetes Metrics Server for more details.
Support to Monitor large size Log File
In the previous agent version, the initial configuration accepted log files with sizes up to 1GB. If the size exceeded this threshold, it would prompt a warning alert.
This restriction has now been expanded, allowing the monitoring of log files with sizes up to 5GB.
See Log Files for more details.
Container Agent Support in Linux-ARM based Architecture
The container agent now supports Linux-ARM-based architecture and incorporates all the features available in the existing Linux-AMD container agent.
Provided Support for MySQL Metrics
OpsRamp has provided support for the following MySQL metrics in MySQL Advanced monitor template:
- Mysql Innodb log waits
- Mysql long running process
- Mysql Index Usage
See G2 Agent Template Details for more details.
Ability to recognize Patches Installed by Sources
In the previous versions, the existing agents did not provide details about the individual accountable for installing a particular patch. With this update, the agent will now show the username who performed the patch installation.
Common Gateway Enhancements
The following enhancements are common to both Classic and NextGen Gateway Appliance models.
View the Count of Monitored Metrics in Gateway
Users can view the count of monitored metrics collected by the gateway for the last 15 minutes. Navigate to the Gateway device details page > Dashboard to access information regarding overview of the number of monitored metrics collected within the specified timeframe.
Enhanced Configuration backup feature to Process large Payloads
The configuration backup feature has been enhanced to efficiently handle large payloads. With this enhancement, the configuration backup process is now optimized to manage and process substantial amounts of data.
SNMP timeout Alerting features to send Alert based on time duration
The SNMP timeout alerts have been upgraded to introduce a time duration-based approach. This enhancement provides more flexibility and accuracy in alerting, allowing alerts to be triggered based on the duration of SNMP timeouts rather than a count of consecutive failures.
Support for Additional Aruba OS Model Devices in Network Configuration backup Module
The Network configuration backup module has been enhanced to support additional Aruba OS model devices. This enhancement ensures that the configuration backup functionality is now compatible with a broader range of Aruba OS devices, accommodating diverse network setups.
Included HPE/Aruba Port-Channel Details in Network Topology
The Gateway has been enhanced to incorporate HPE/Aruba Port Channel details in the topology response. This enhances the visibility and comprehensiveness of network topology information provided by the Gateway.
Users can now gain insights into the Port Channel details associated with HPE/Aruba devices directly from the topology response, allowing for a more comprehensive understanding of the network infrastructure and regarding Port Channel configurations.
Support for Microsoft Extension of OAuth 2.0 Authentication
OpsRamp supports Microsoft extension of OAuth 2.0 authentication. The following optional message body parameters will now be supported when making a request to the token.
- Resource
- use_windows_client_authentication
- requested_token_use
- assertion
- csr
- csr_type
- x5c
- tbidv2
See HTTP/HTTPS Synthetic Monitors for more details.
Support for individual transaction times in HTTP Synthetic transaction
HTTP Synthetic transaction actions to support individual transaction time. Users can choose to switch to individual transaction times for each action rather than the current cumulative time in synthetic transactions. This will help users to track the time spent in each of the actions as a metric.
See SCRIPT – HTTP Transaction for more details.
Security Enhancement
- Application security improved by upgrading vulnerable jars to the latest version from maven library.
- Stopped logging the sensitive information in the gateway logger file while restarting some services vprobe, appliance, etc.
- Stopped logging the sensitive information in the gateway logger file while enabling Synthetic Agent.
Bug Fixes
- The issue where users could not retrieve the latest metric information for the vprobe performance template has been resolved.
- Fixed issues with utilization and Network Interface Cards (NIC) status metrics for Pure Storage.
- Resolved the issue where a hardcoded value was being used for MYSQL monitoring metrics when the device did not provide a metric value response. Now, no metric value will be sent in the following cases.
(mysql_Replication_Status,mysql_slave_IO_Running_Status,mysql_slave_Sql_Running_Status metrics)
NextGen Gateway Enhancements
IP range Support in K3s Installation
The OpsRamp collector tool has been enhanced to support IP range configurations for K3s installations. Users can now specify an IP range within the Kubernetes network range to be allocated during the installation process. This enhancement provides increased flexibility and control over the network configuration within the specified IP range.
Note: This feature is only available for users who are using OpsRamp provided ISO/OVA.
See Installing NextGen Gateway in HA Mode for more details.
See Installation of NextGen Gateway using ISO for more details.
Introduced distributed Redis cache for SDK Apps
OpsRamp introduced a Redis distributed cache for SDK apps to improve app performance. This improvement will pave the way for supporting gateway clustering in upcoming releases.
Bug Fixes
The Gateway tunnel experiencing flapping while loading the LB/Proxy IP from the gateway service has now been addressed.
Security Enhancement
OS level security has been improved by upgrading OS packages to the latest version from Ubuntu 20.04 repository and application dependency packages.
Classic Gateway Enhancements
Verify the SNMPv3 Credentials Working Status
Users can now verify the functionality of SNMPv3 credentials directly from the Gateway web UI.
This feature allows users to verify the SNMPv3 reachability and response for a device without logging into the gateway.
See Configure SNMP V3 trap credential for more details.
Optimized the Gateway OVA Deployment
The Gateway OVA (Open Virtual Appliance) deployment process has been improved to make configuration tasks easier and setup more efficient. Users can now easily configure the following settings during the deployment:
- Network settings
- Perform gateway registration
- Specify NTP servers
- Enable/disable the Squid proxy
See Deploy a Gateway on VMware ESXi Server for more details.
Security Enhancement
- OS level security has been improved by upgrading OS packages to the latest version from Ubuntu 22.04 repository.
- User authentication is evaluated when logging in through the shell. If users have direct access to root with sudo permissions, they can run commands without entering a password.
- Restricted some of the file permissions on the Gateway from unsafe settings to prevent unauthorized users from modifying or corrupting them.
- We have added authentication to the default postgres user account in the PostgreSQL database.
Bug Fixes
The classic gateway webUI was broken due to “Rate limiting” introduced on the Gateway API call to avoid DOS attacks has now been resolved.
Windows Gateway Enhancements
Alerting capabilities for Remote PowerShell Monitoring
Alerting capabilities for Remote PowerShell Monitoring have been improved, moving from device-level to monitor-level alerting.
Users can now receive more detailed alerts for Remote PowerShell Monitoring, allowing for better understanding and quicker responses to a specific monitoring event.